KaaIoT IAM Cloud: Identity and Access Management SaaS Solution
Identity and Access Management is a key part of modern enterprise-grade software solutions, and enables companies to granularly manage their users’ access depending on roles and responsibilities.
An IAM system features identity management tools for secure user authentication as well as authorization tools for flexible allocation of access rights to various system resources, such as applications, databases, connected devices, and digital assets. It also provides accounting/audit features to measure and analyze user access to system resources, duration of user sessions within the system, and amount of data transferred during those sessions.
In IoT, IAM plays a vital role because of the great variety of potential system resources that different users may have access to - smart devices, IoT dashboards, data analytics tools, IoT admin tools, etc. Users may also have different types of access rights - full access, view only, limited editing rights, etc. and be subject to complex, multi-level organizational access policies.
In order to meet our clients’ need for a full-scale, independent IAM SaaS solution that can be used within any software ecosystem, we are currently in the active phase of implementing the KaaIoT IAM Cloud. Backed by our team’s profound experience in enterprise security, IoT, asset management & authorization, and enterprise user management, this is going to be the best-in-class IAM cloud solution for IoT and beyond!
The KaaIoT IAM Cloud will enable companies to easily manage access policies for their digital and physical assets, accurately represent their organizational security policies within their digital space, create complex hierarchical entities for fine-grained access control, and scale up their security operations to millions of assets, devices, policies, etc.
Also, KaaIoT will provide consulting services and technical support for KaaIoT IAM in order to ensure the best experience for all of our clients and users.
KaaIoT IAM in a Nutshell - Authentication, Authorization, and Accounting in the SaaS Format
IAM consists of three major elements (triple A): authentication (identity management), authorization (access management), and accounting (audit). KaaIoT IAM excels at all these three areas with the specific emphasis on flexible access management, which is currently one of the biggest security pain points for large enterprises.
For authentication, KaaIoT IAM provides multi-tenancy support for external IDPs such as OAuth, OpenID, SAML, etc. It also supports the federation service (LDAP) for each tenant (see the picture below).
For authorization, KaaIoT IAM provides tools to manage resource permissions with minimal hassle and virtually no code. For example, you can easily map job functions within your company to user groups with roles. Users get access only to what they need to get the job done, and admins can easily grant default permissions to entire groups of users.
For accounting, KaaIoT IAM features an analytics module that enables admins to log user activity data, measure various user session data, and build analytical reports.

Emphasis on Fine-Grained IAM Authorization
The biggest advantage of KaaIoT IAM is its fine-grained authorization (access management) functionality that addresses the key pain points of enterprise users. Now they can represent any level of organizational complexity and access rules in their software solution, without the need to custom-code their own IAM system.
KaaIoT IAM enables companies to create highly granular access control policies for their digital and cyber-physical assets based on high-level parameters, such as resource type, as well as low-level attributes, such as device status or IP address.
KaaIoT IAM utilizes both identity-based and resource-based policies defined within your organization. These policies help ensure that the appropriate security protocols are always in place when granting access to any resources available from your software system connected to KaaIoT IAM.
For example, as displayed on the picture below, user ThomasOwens can access, configure , and manage resources X, and Z. Resources X, and Z also confirm those rights for user ThomasOwens. However, while user PhillipFischer can access resources X, and Z, resource Z specifically denies access to user PhillipFischer. In this way, using both identity-based and resource-based policies, you can have double protection for your system resources.

No-Code Policy Configuration
It is a common situation that an organization’s internal structure and security policies get complex fast, especially in IoT-based ecosystems. Projects, work groups, connected devices, and permissions are all in a constant flux.
To ensure that your company always keeps up with the pace of changes, KaaIoT IAM has been designed with simplicity at its core: a clean, universal policy format that allows you quickly update and manage access control policies across your entire IoT ecosystem. You can see the policy format below:
{
"Statements":[
{
"Actions": [...],
"Resources": [...],
"Principals": [...],
"Effect": "allow/deny"
}
]
}
Within this format, the KaaIoT IAM system uses statements, actions, resources, principals and effects.
- Statements - a container for policy elements, where the user can define as many elements as needed. (Allow or deny something)
-
Actions - a list of scopes that should be handled by IAM (Specify what actions will be applied to what resources)
Example:
epr:*
epr:endpoint:read
epr:endpoint:update
epr:endpoint:delete -
Resources - a list of resource names to which statements will be applied (select for which resources you allow which actions; can allow all actions with *)
Example:
iam:c64f7cf0-f792-47a4-9ee5-cb296946f01f:epr/*
iam:c64f7cf0-f792-47a4-9ee5-cb296946f01f:epr/c64f7cf0-f792-47a4-9ee5-cb296946f01f - Principals - a list of users, groups, tenants (user account name)
- Effect - can be either allow or deny
When it comes to performance, our IAM solution can support virtually any number of policies and ensure stable response with 200ms latency for up to 100 million managed resources!
How KaaIoT IAM Authorization Works
The following diagram illustrates how KaaIoT IAM authorization works and, specifically, how it makes a decision to allow or deny user access to a certain resource.
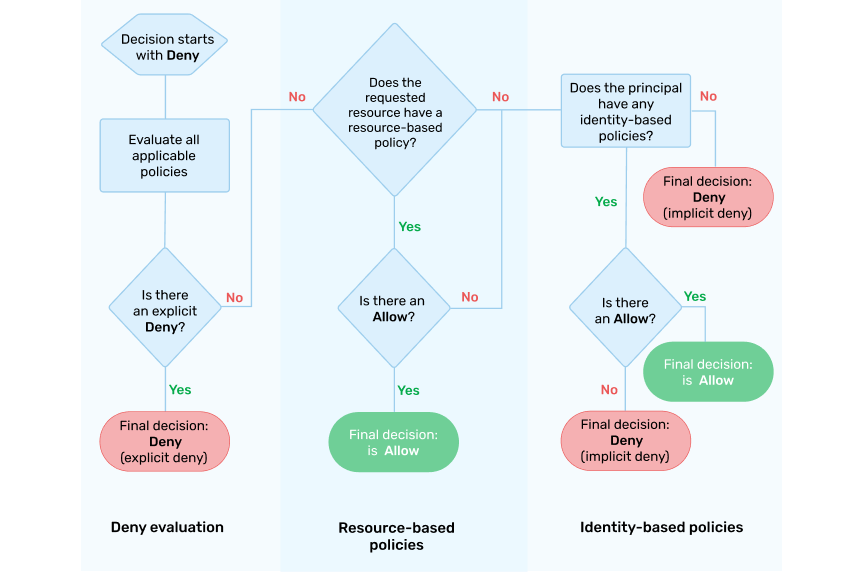
First of all, the IAM service checks whether there’s at least one policy denying access to the principal (user, user group, etc.). If there’s at least one, then IAM takes the decision to deny access. If no such policy exists, then resource-based policies are checked next. IAM checks policies that allow access to the exact principal, and opens access to this resource if the answer is positive.
If no resource-based policies that allow access to the exact principal exist, then the IAM service checks if the principal has any identity-based policies. If there are none, IAM issues a ‘deny’ statement. If the principal has an identity-based policy that allows access to the resource, then IAM makes a decision to allow access to the resource.
All authorization settings are flexible and the tenant owner can set up multiple customers with their own permissions. In turn, customers can have their own users (directories) and own Admins, Developers, Support Specialists, etc.
Developer-Friendly IAM with Open-Source Options
As the creators of one of the most developer-friendly IoT platforms - the Kaa IoT Platform, KaaIoT is now implementing the best-in-class, developer-friendly IAM solution. We also plan to release open-source bundles and integration libraries for our IAM!
For those who want to create a highly personalized IAM solution and build value-added services on top of it for their own clients, KaaIoT IAM will be a perfect fit.
Among other features that IoT engineers and IoT security admins could fully appreciate are the following:
- Advanced user management integration using external IDP providers (SAML, OAuth2, OpenID)
- Federation with LDAP
- Cross tenant policy evaluation
- SDK’s for common languages (Java, Python, Golang)
- and other great features that you’ve been looking for in a full-scale IAM SaaS!
Enterprise Identity and Access Management Use Cases
Consider the following Kaa IAM use case scenarios for enterprise companies that demonstrates some of its capabilities and flexible usage:
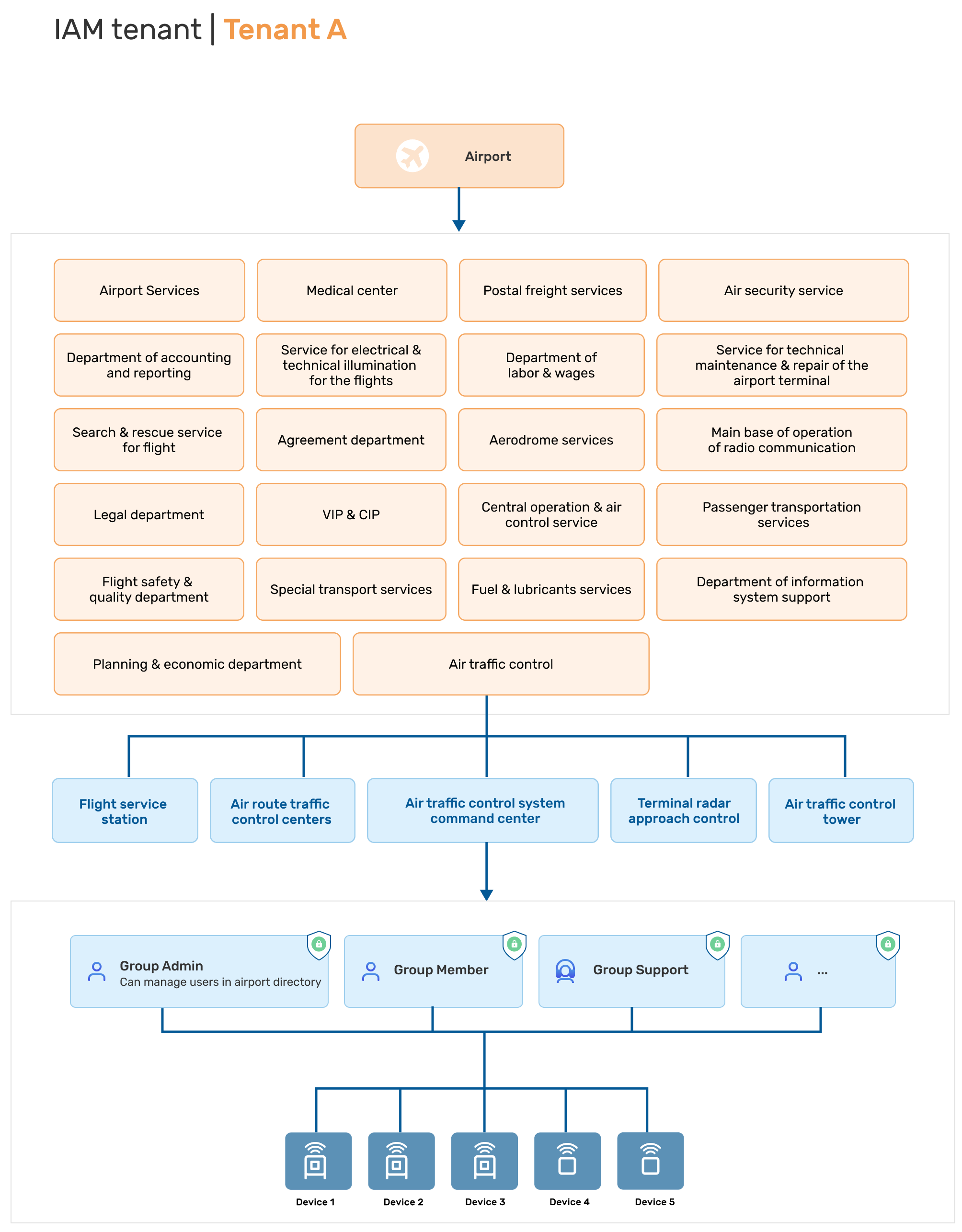
Scenario #1: Large company with multilevel authentication and permissions system
In the first diagram, we have an example of an airport as a Kaa Cloud Tenant, where the tenant owner has 22 groups representing the airport branches. Every group has permissions to create and manage their own organizational units with their own hierarchy and user roles. The diagram shows the internal structure of one of the groups, Air traffic control. Group Admins can create users and additional subgroups as well as distribute permissions as required at every level of this hierarchy.
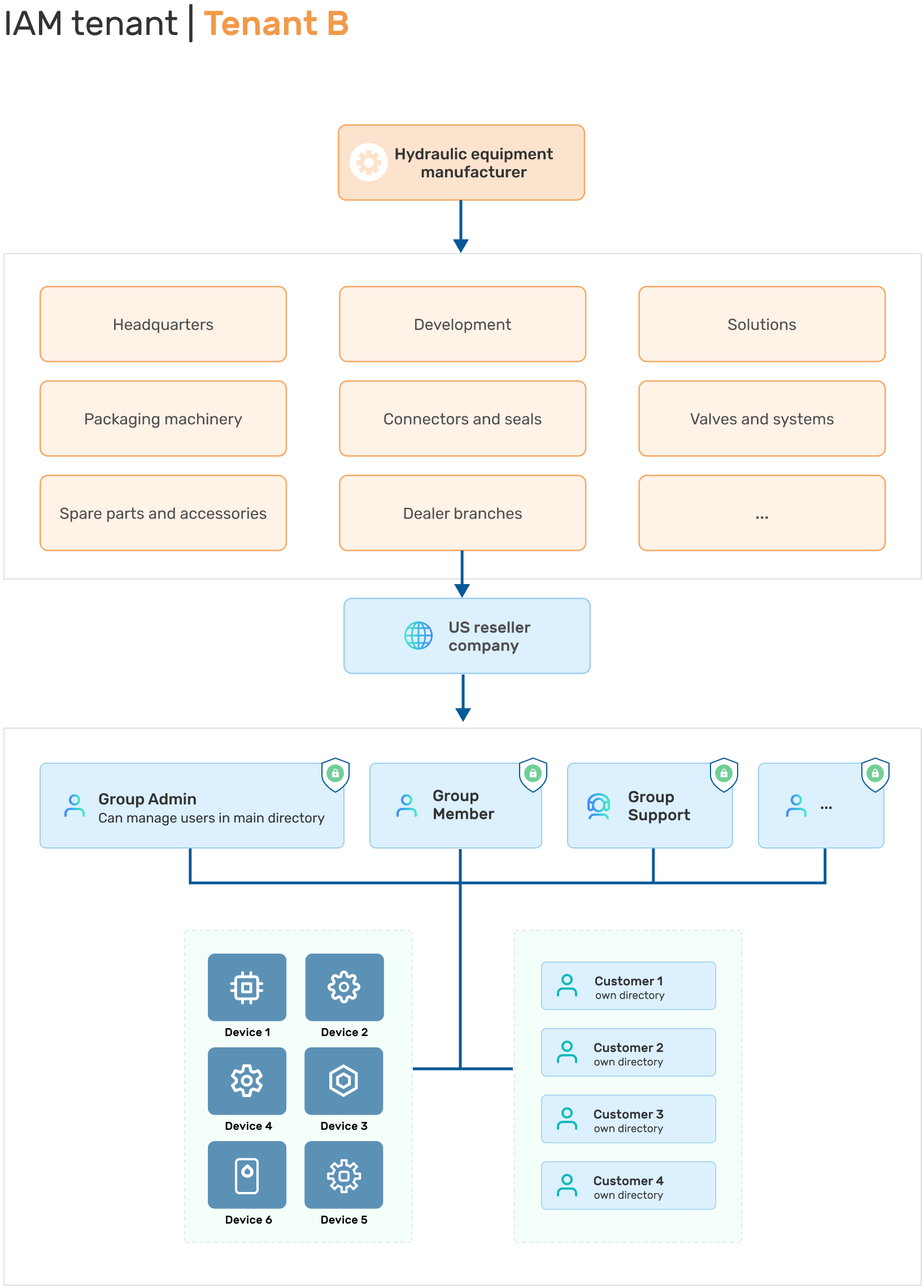
Scenario #2: Industrial equipment manufacturer with resellers and dealers
The industrial equipment manufacturer displayed in the second diagram has multiple subdivisions, from Sales to Solutions, with every one of them having their own organizational units. Resellers and dealers have their own customer support units with direct access to customer devices. Customers can create their own users as well. Access to the devices status, maintenance reports, etc can be distributed by Admins in a flexible way.
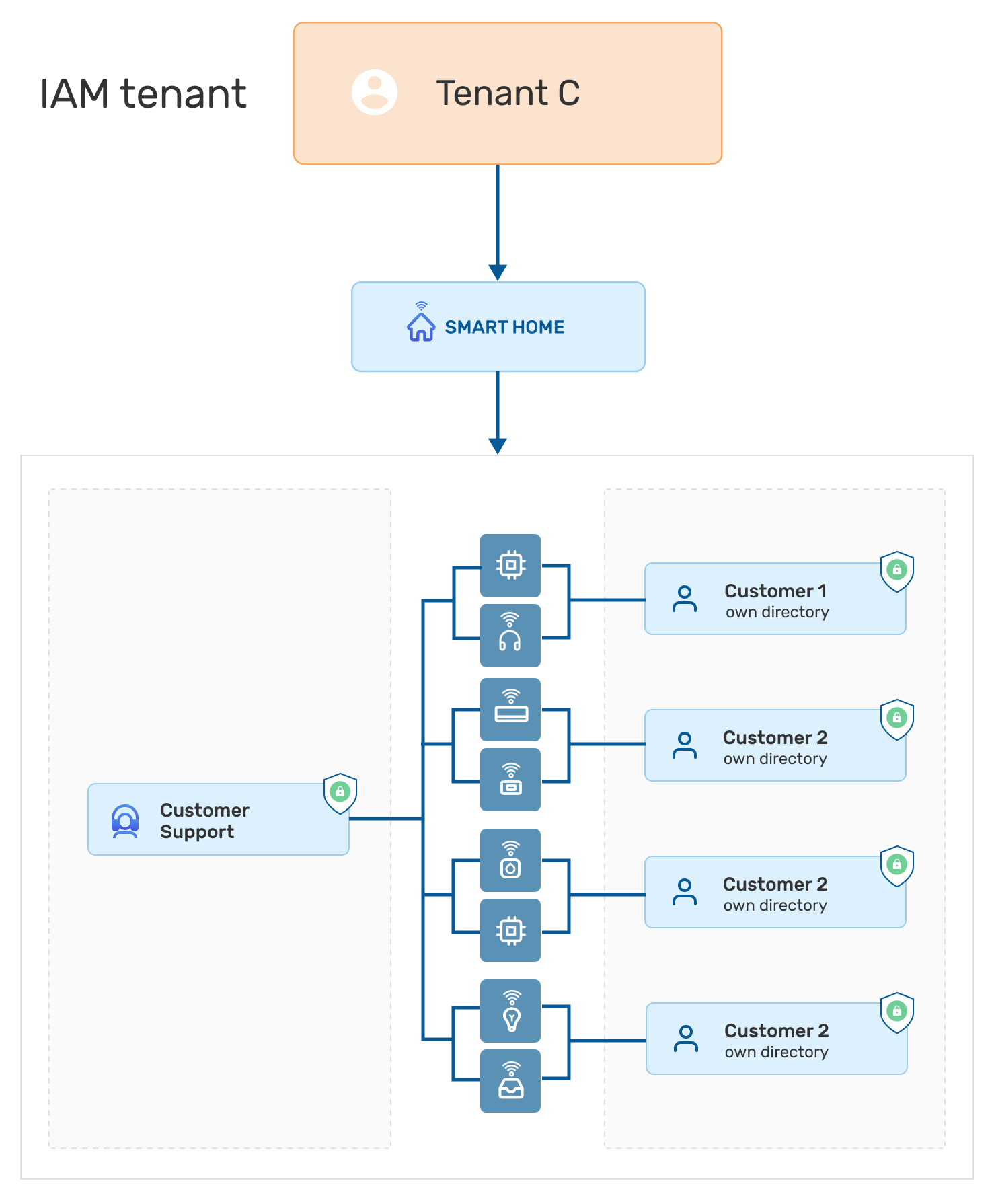
Scenario #3: Smart home solution provider
The Kaa cloud tenant owner in the diagram has full access to all devices data, telemetry, and device owners’ data, including their directory statistics, events, and user roles. Device owners have access only to their device data and cannot see each other’s tenants. Access to the devices can be shared by the device owners to their Directory members. The IAM service controls authentication and authorization events in the Kaa tenant and distributes roles and permissions on all hierarchy levels.
KaaIoT IAM as Part of Kaa Cloud and as Independent SaaS
Kaa Cloud, an IoT SaaS powered by the Kaa IoT Platform, will offer KaaIoT IAM as standard in the form of a user-friendly IAM interface, also combined with the user analytics and user dashboards.
All the users of Kaa products, including Kaa Cloud, will soon be able to achieve a state of security where it is easier and safer than ever to implement a variety of security policies for authorization and authentication, as well as ensure security audit.
However, as we’ve mentioned above, KaaIoT IAM will be an independent IAM SaaS product that can be used within your company’s unique enterprise software landscape, even for implementing value-added IAM services for your own clients.
With several years of product evolution backed by thousands of satisfied users around the globe, KaaIoT never stops innovating! Contact us to learn more about KaaIoT IAM.