Kaa Identity and Access Management
Comprehensive, unified user resource access and permission management for advanced, secure solutionsSecure and flexible assets control
Kaa IAM integration allows orders of magnitude faster time-to-market for SaaS and enterprise products
Enable easy access to your IoT resources for individual users and user groups at any time
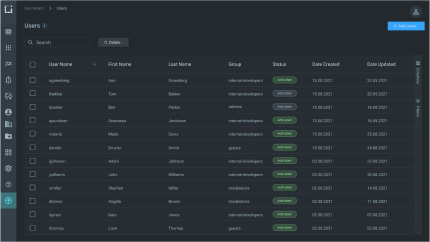
Get full user activity audit and view event history for users and user groups, run queries and search logs
Set up advanced granular permission control on every organization, entity and asset level in your IoT environment
Simplify access scenarios for every level of control over resources or IoT devices in hierarchical organization structure
Unlock opportunities of expanding to the new markets or market segments on your IoT solution roadmap
Identity & Resource Access Management with Kaa IAM
The Kaa IAM Identity and Access Management solution simplifies access control and asset management of both implemented IoT solutions and the IoT solutions being built. Under the hood, the whole IoT assets/resources management system is built from complex networks of devices, sensors and other technical structures that managers need to run effectively without spending too much time for in-depth control of every minor operation. The Kaa IAM solution helps system managers see the status of physical and virtual assets and derive business decisions from quick, real-time data visualizations or reports.
Enterprise organizations need to precisely manage access to their fleet of whatsoever, and here is where Kaa IAM comes into play. Providing operational transparency to factories, power plants, vessels, vehicles, robots, devices, people, people & devices - Kaa IAM engine augmentation capabilities are virtually endless.
IAM roles and permissions are very flexible and convenient ways to distribute access for any type of hierarchy of their cloud services. Hierarchy of access and its flexibility is also the key in multi-branch companies with distributed offices and the need to securely provide and switch operational resources to authorized employees.
To avoid devices or resources being controlled by someone else, companies develop custom solutions that require quite a lot of effort to deliver. Security is vital here. All kinds of companies over multiple industry verticals, from consumer devices to hotels, put security first, and IAM successfully helps them solve these challenges.
Common scenario for IAM: Consumer Electronics
Most of modern consumer electronics demand access to the Internet to be operational. Let's take an example of a consumer electronics company, HVAC or a heater producer with IoT-enabled devices or assets.
Once the IoT devices or assets are connected, a company can access them and check up maintenance parts status, such as filters, battery, etc. As a customer, you would require operating your device remotely and having it maintained by someone - that’s a general request for all consumer electronics. Kaa out-of-the-box, quickly configurable IAM solution can help companies provide such services to customers without the need for in-house development.
- Company A is an IoT device producer
- A local company B would like to provide IoT device filter maintenance
- Company C is responsible for the motor (relay, any other part) maintenance
- Consumers provide information to Company B and C only about the status of their components.
- Company B must not intersect with company C data and related devices.
- Company B and C may have subcontractors and other business entities etc.
- Consumers don’t provide control over their equipment to companies B and C
- All IoT device chain participants get better visibility into their product and high value business data on how their product is used and maintained
- Spare parts distributors better adjust their supply chain
- Company managers save costs while responding to replacement notifications timely, and cut disaster rates with the equipment going faulty
- Insurance companies save costs tracking exact status of assets
- Companies save costs locally providing central resources maintenance
We’ve mentioned a basic scenario above, but with several administrator levels complexity increases - and it's where Kaa IAM takes control, solving this challenge effortlessly. For instance, you’re selling the equipment to a hotel and the hotel administrator needs access to temperature control. With Kaa IAM, we just add over one or more device management levels and that's it.
Your IoT devices and resources will require flexible access to the sensor data distributed between different numbers of users and groups. Kaa IAM eliminates the need to continually rebuild your custom solution for multiple scenarios over and over again.
To avoid this long, troublesome journey with the unpredictable and continuously increasing spending, you can get the solution out-of-the-box with any number of layers, granularity, groups, organizations, assets, or augments already custom made for your case.
Multiple service companies would gladly feed off the opportunity to create more custom solutions that would be more complex and would be a constant revenue source. But the key benefit of the Kaa IAM solution is actually removing the need for custom solutions/development of complex infrastructure, while saving costs and allowing faster time-to-market.
Features
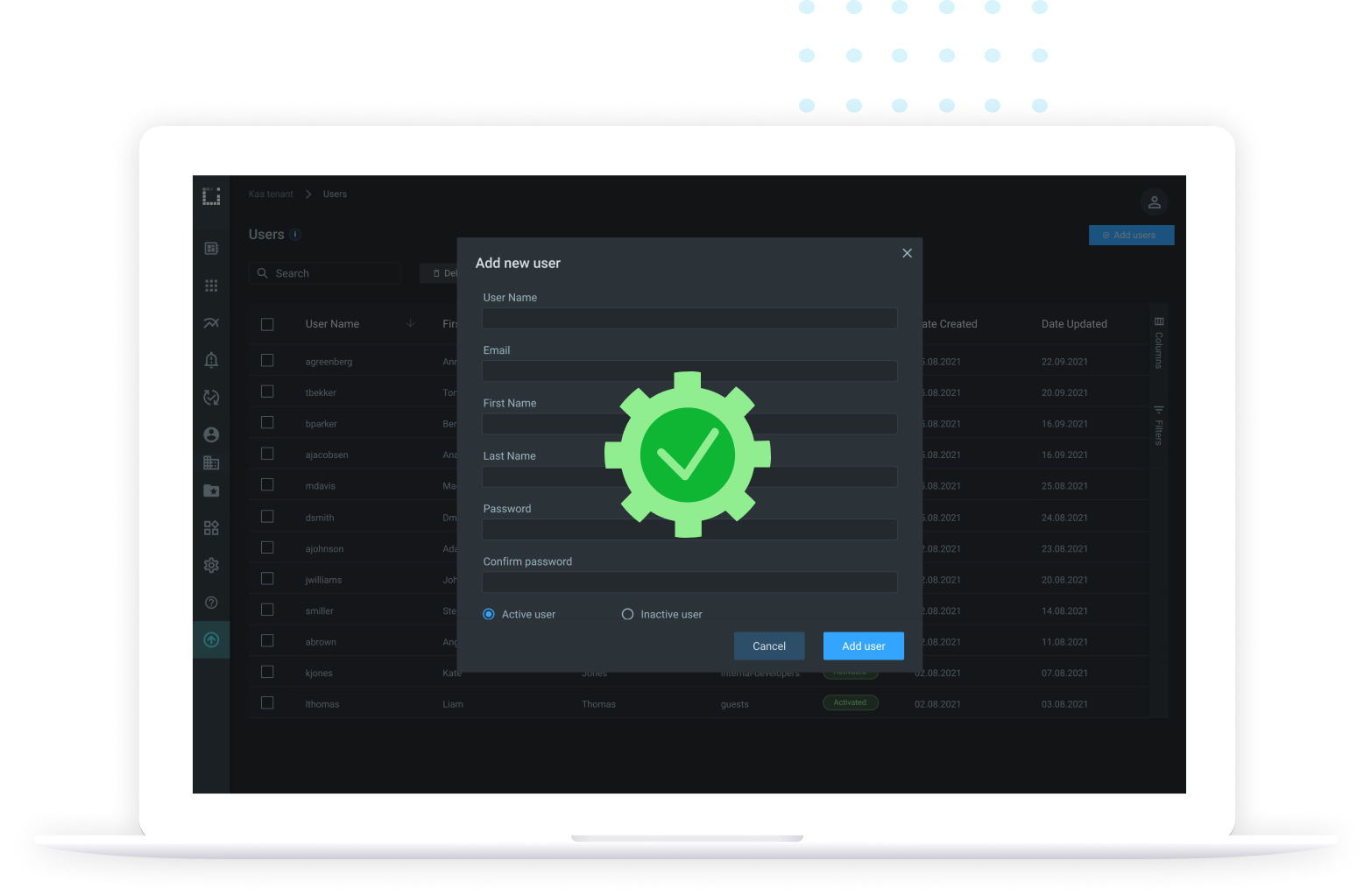
Advanced user management integration using external IDP providers (SAML, OAuth2, OpenID)
IoT solution admins configure user attributes such as emails, first and last names, to propagate from the IDP to the service provider. You can then send custom attributes to apps through OpenID tokens.
Federation with LDAP
Securely convey identity and authentication information via multiple networked systems. Provide users with single sign-on access to systems across your enterprise.
User authentication and authorization
Grant access to IoT resources only to genuine, verified user identities with the correct credentials. Give the users permissions to access specific resources, such as endpoints, dashboards, and devices, and control client privileges.
Multi-factor authentication
Set up two or more verification factors to provide secure access to users and user groups to your IoT resources, applications, or solutions. Utilize strong Kaa IAM to enhance your IoT solution security and keep your data safe.
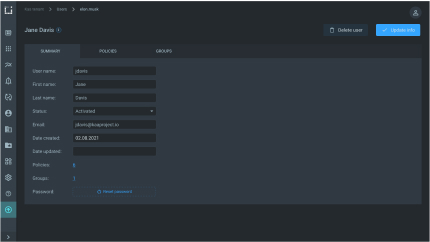
Identity and resource based policies
Attach identity-based policies to users or groups, or assign independent roles. Specify what permissions users have and what they are allowed to do in the system. Implement resource based policies to key resources such as IoT applications, dashboards, or endpoints.
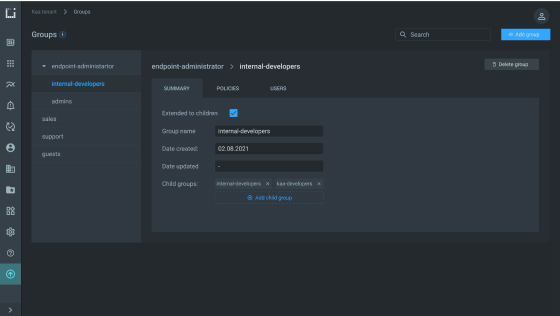
User groups support
Create and manage user groups to specify permissions for multiple users at once. Add or remove users from groups to change user privileges quickly and easily instead of editing new user permissions individually.
Cross tenant policy evaluation
Dynamically generate policies to implement secure tenant isolation. Configure individual roles or roles shared by a group of similar functions and limit the permissions assigned to roles.
SDK’s for common languages
(Java, Python, Golang)
Faster development of applications on Kaa in the programming language of your choice. Access sample code and successfully build your projects.
Practical benefits of IAM integration

Unparalleled scalability for virtually unlimited number of managed resources

Authorization templates for various types of industry use cases: B2B, B2C, B2B2x, etc.

Increased operational efficiency and improved system uptime

Out of the box integration with common software development technologies